Goal
Receive asynchronous updates for payment authorizations so your internal transaction state remains accurate and reliable.Steps
Step 1: Configure webhook delivery on authorization requests
What you need to do
Include webhook configuration when submitting authorization requests so Push can notify your system of final payment results.How to do it
When calling authorize-payment, provide:- A
webhook_urlwhere Push will deliver webhook events - A
webhook_secretused to verify webhook authenticity - A
tagthat maps webhook events back to your internal transaction record
Step 2: Receive and process webhook events
What you need to do
Expose an HTTPS endpoint that can receive webhook events from Push, verify their authenticity, and update your internal transaction state.How to do it
- Create a HTTP endpoint at the configured
webhook_urlcapable of receiving POST requests. - Verify the webhook signature and timestamp for each request (see security).
- Parse the webhook payload and update the transaction record in your database accordingly. Please refer to the reference guide for the structure of the webhook payload.
Security
Webhooks deliver data directly to an endpoint you control over the public internet. Because they are invoked automatically by Push, webhook endpoints must be explicitly secured to prevent unauthorized requests, data tampering, and replay attacks. Without proper verification, a malicious actor could spoof webhook requests and falsely mark payments as approved or declined in your system.If your cloud data environment restricts network access from external IPs via a firewall, you may need to allow inbound
traffic from Push IP addresses in order to receive webhook requests.
Push webhook source IP addresses
Push webhook source IP addresses
Production
44.238.180.175Sandbox 34.209.246.44Signature verification
When awebhook_secret is provided, Push signs each webhook request using an HMAC-SHA256 signature derived from the raw
request payload. This allows your application to verify that:
- The request was sent by Push
- The payload has not been modified in transit
- Extract the signature from the
X-Webhook-Signatureheader - Read the raw request body as bytes (before parsing JSON)
- Compute an HMAC-SHA256 signature using your
webhook_secretand the raw body - Compare the computed signature to the received signature using constant-time comparison
- Reject requests with invalid signatures (
401 Unauthorized)
Code examples for signature verification
Code examples for signature verification
Timestamp Verification
Thetimestamp field in the webhook payload indicates when the webhook was created. To prevent replay attacks, verify that the timestamp is recent (within 10 minutes).Verification Steps- Parse the
timestampfield from the payload (ISO 8601format) - Compare with current time
- Reject requests older than 10 minutes (return
401 Unauthorized)
Independent Ordering
Webhook delivery and authorization responses are independent and may arrive in any order. Your system must handle both scenarios by ensuring that the internal transaction record is committed to the database before the call to the authorization endpoint:- Webhook arrives first (before authorization response)
- Authorization response arrives first (before webhook)
Sequence diagram illustration
Sequence diagram illustration
Sequence diagram illustrates the two possible scenarios of ordering between webhook delivery and authorization results.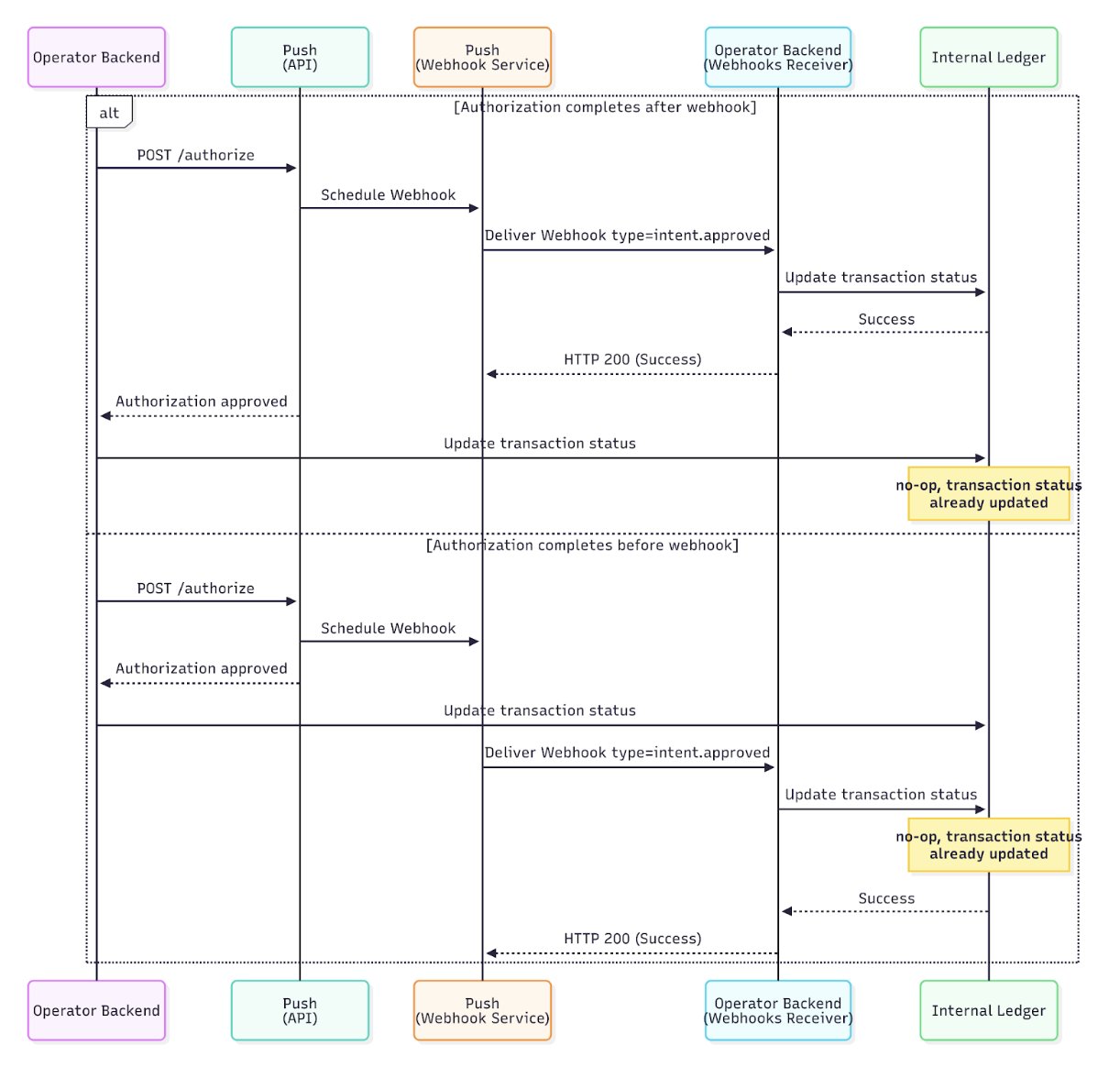

Idempotency
Push provides at-least-once delivery for webhooks. Your application must handle duplicate webhook deliveries gracefully using database transactions to ensure idempotency. In the case of a duplicated webhook delivery from Push either due to an error or timeout from your callback handler, you should discard the request and return a200 OK.
If Push does not receive a200 OKresponse from your webhook endpoint, delivery will be retried with exponential backoff.
| Environment | Retry Behavior |
|---|---|
| Sandbox | Up to 3 attempts |
| Production | Up to 40 attempts over 3 days, then marked as expired |
Integration checklist
- Payment requests include the
webhook_url,webhook_secret, andtagparameters - Webhook endpoint is reachable over HTTPS from the Push IP addresses
- Webhook signatures and timestamps are verified before processing
- Duplicate webhook deliveries are handled idempotently